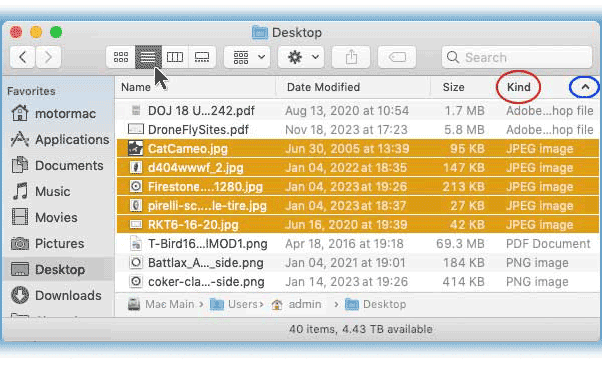





 The Basics:
Web-based threats, email spoofs, keyloggers and spyware..... We all face threats from bogus sites, apps, spoofs, redirected comms and data breaches. Don't be a victim.
Apple has all but eliminated the threat of viruses, but that's not to say Mac users can be complacent about security. Keep your current OS updated, know who you're dealing with, and never download anything from an unknown source. The most significant threat to security is physical access to your computer or device. Wireless and remote threats are managed by maintaining security protocols and proper passwords. This page is about Mac security and what you should know to protect yourself - and what you should avoid. Malicious software (Malware) is not easy to remove
Avoid all anti-virus apps, cleanup/maintenance apps, PDF readers, video viewers, and "free" utilities. Once installed, they needlessly consume storage space, waste CPU cycles and can cause havoc. Even some apps found on Apple's AppStore are less than useful. The only maintenance app you need comes with the System: Disk Utility.
Security on steroids
Since the end of OSX (Catalina), Apple has gone on a security binge with new "features" that can easily ruin your day. The OS is now on its own locked partition, meaning no access, no OS backup, and (possibly) no downgrade if a new OS install isn't to your liking - a primary reasons for having backup on an external drive. Security options lock out access to troubleshooting and data recovery from another Mac or external device. Add Apple's new Activation Lock, and your Mac might be bricked. These "features" are all on by default. If you know what and where they are, these options should be disabled to prevent potential disaster; more info in "Over-The-Top Apple Security" section below.
|

 PDF Readers Was a time when Portable Document Format (PDF) was a new file type from Adobe and required Adobe Reader, but that was long ago. PDFs are built-in to the MacOS and Apple provides the Preview.app to deal with PDFs. There are a lot of PDF utility apps out there which are not necessary, and some are merely scams to convince you to download and install whatever garbage they contain. Same with "video viewers" and many other bogus apps out there.
Malwarebytes
This program was originally designed to stop pop-ups on the internet. Designed by a gentleman named Reed and available on Apple's discussion site, it was a free giveaway for many years and became quite common. It was so successful, the good Mr. Reed sold the program and it became a commercial app. Unfortunately, it now includes something called 'Threatdown" and has been redesigned in such a way that makes removal very difficult. This app is now best avoided.
Cleanup, speedup, fixup apps
Programs that claim to clear cache files, remove unnecessary software and improve performance are seldom worth the trouble. They will try to impress you with scans and charts and graphs, while needlessly consuming CPU cycles and wasting your time. Deleting cache files only means the System will have to recreate them, there are much better ways to remove unwanted programs, and usually such "maintenance" apps merely put their own interface on processes built into the Operating System. They have little or nothing to offer.
"Do I need an anti-virus program?"
No. Nothing gets installed on a Mac without entering a password and clicking an install button (after a warning or two). Viruses cannot come onboard without your knowledge, permission and password - which is why there are so many fake apps floating around on the internet. Companies that make anti-virus software would be foolish to ignore the Macintosh market, so they will sell you their product despite knowing it's useless. Some such apps waste precious drive space and can become a bigger problem than any virus they pretend to prevent.
Before downloading and installing software from an unknown source, take a minute to search the 'net for it by name and see what is being said about it; if there are lots of people trying to remove it, you might want to reconsider.
|




 By definition, a computer virus must have three specific traits:
"I think I've been hacked!"
Malicious software - aka malware - comes in a wide variety, from phony updates to bogus apps of all kinds. Types of fraudulent apps include fake cloud backup, bogus online password management, maintenance utilities, readers, viewers, players and assorted other "helpful" apps. If you enlist the services of cloud backup, you'll be sending them all your data, legitimate services and bogus ones alike. Same goes for password management services that store your passwords. Do you know who they are or where they're located? No password, encryption, VPN or security measure can protect you from voluntarily engaging thieves or downloading garbage. No, you haven't been hacked. Banks get hacked, Social network sites get hacked, Google, Yahoo (et al), credit sites and retailers get hacked. People generally don't get hacked, aside from an occasional celebrity or maybe an acrimonious divorce. "Hacked" is one of those terms that sounds good, but usually means scammed.
Know who you're dealing with.Free, demo, trial apps, bogus updates, PDF/Word readers, video viewers, and a slew of Mac fix-up apps - including paid versions - are as close to viruses as we get on the Macintosh platform. Don't go there.
 Best advice:
If you limit downloads to Apple's App Store and only deal with KNOWN sources by making certain the address in web browser is legitimate, you'll have little to worry about. That's the short version - more info and details follow.
(Also see our Rants page for more on security concerns.) |

 As a friend says, "you have to be smarter than the tools you work with." Just because that email says it's from a friend - doesn't mean it is.
Of course, if you rely on mail thru Yahoo or Google or other online service, the security of your email (including your address book and whatever else is attached to your account) is out of your hands and up to the service provider. They get hacked on a regular basis, so don't be surprised if it happens to you and suddenly everybody you know is getting spam with your name on it. Such security breaches occur all too often, and that's the risk you take when using free online mail services. Your choices are to change your email address or just wait until it blows over (which it eventually will). |

 If it comes looking for you, you don't want it. Real-world internet security concerns (regarding Macs) revolve primarily around downloads that may be deceptive and/or damaging if installed. This cannot happen without your active participation and knowledge. If you see some unexpected message popup while surfing the 'net, and it wants you to download, scan, update or install something, don't do it. Cancel/close and ignore the message.
In the case of email attachments, a virus might well be attached to some email message you receive, but these are typically incapable of doing any harm to a Macintosh. However, while it cannot affect your Mac, if passed along to a Windows machine where its code _can_ execute, it might attack the Windows user. Delete it.
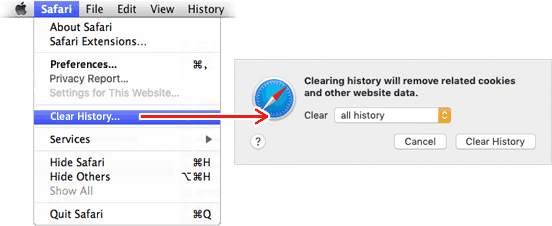
Best advice is to simply be aware, be suspicious of uninvited prompts, and don't click anything you're not absolutely certain of. Clear your history and delete cookies periodically (although you may have to hunt for some of 'em - see below), open a new browser window if you like (File menu -> New Window) and use your bookmarks or type-in the address you want to go to. Cancel unexpected options and avoid anything even faintly suspicious.
  The term "Malware" (short for malicious software) refers to a variety of bad-nasty things floating around in cyberspace, including viruses, spyware, Trojan horses, and a host of lesser types (in terms of potential damage). Rule of thumb: If you need some app or software, player, update or utility, go to the source and get it. DO NOT download anything that comes looking for you!
Spyware is a whole different animal. This category includes commercial programs designed to track computer use and record keystrokes, but these are not necessarily viruses. Popular with parents, security departments and company bosses, spyware provides indisputable proof of computer use and activity. That's the legitimate use of spyware: Parental control, tracking company time and tracing activity. But - spyware can also be used to steal passwords, banking and credit card info or other personal data for purposes of theft. Properly installed spyware requires physical access to machine for an extended period of time, a few hours or more. Once in place, professional spyware is - by design - difficult to detect. The cheap and cheesy types are rather obvious. A Trojan Horse - like the Greek myth - requires your active participation to download and install before it can do its thing. Therefore, it must trick you into bringing it onboard by masquerading as something attractive or pretending to be something it isn't. Here's an example, one of hundreds popping-up on the internet these days:
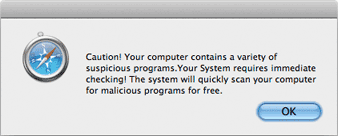 Text is laughable - doubt if many who read this would fall for it
If you click OK, the next window will be a "free download" of the Trojan disguised as an anti-virus app. If you are gullible enough to download, you will then have to enter your admin password to install it and you'll be warned that you're about to install an app from the internet. Just close the window, quit browser if you have to, or trash the file before installation and you'll be fine.Some of these Trojans will put up a window listing a few files it claims are infected and should be "scanned" immediately. We've seen many examples of this type over the years, and most look very much like a genuine Mac application. (We tracked one to Belize, by way of Germany, with a contact number in Russia.) Fortunately, they're easily removed and relatively harmless but always best avoided. While the Microsoft Windows world has long been awash in viruses that cannot infect the Mac, that doesn't mean Macs are 100% safe. The Macintosh remains largely immune due to proactive prevention by Apple at the core of your MacOS, but there are lots of other threats out there besides viruses. Nothing gets installed on a Mac unless a password is entered and installation is approved. The only protection you really need is common sense. |

 Privacy versus practice
The World Wide Web should be free, unregulated, uncensored and untaxed - but it also needs to be approached with care. Dealing with the internet means you can assume you're being tracked and you're quite likely to encounter something nasty along the way.
If you have a network and internet connection, you must protect it. Use a router with a firewall and secure password, especially since most routers include wireless functions. Normally it's just a matter of selecting the best available protocol and setting a password - never use preconfigured passwords that ship with devices, create your own - and remember to write it down. Connecting to networks out in the wild is another matter entirely. Consider these to be wide-open and unsecured, and never transmit anything sensitive over a foreign wifi network. There have been reports of thieves setting up adjacent networks with names matching legitimate ones; that "Starbucks" network might be Starbucks or it might be some bozo out in the parking lot. This type of spoof can be difficult to detect or verify. You can also assume a general lack of privacy, as virtually every app you use is phoning home with some data yo target ads or check for updates, whether on a computer, tablet or phone. GPS-equipped devices may attempt to map wireless access locations by sending coordinates and network info. Computer and software makers collect and send data, including OS, app versions, and machine specs. Any audio device may be transmitting all it hears (with or without your consent); phone apps are notorious for trampling on privacy. There are legitimate types of data collection used to enhance product performance and provide assistance, but the line between that and eavesdropping is disappearing. Pay attention to network activity
The key (on a Mac) is that nasty stuff, like all software, requires login password and permission to be installed. Once onboard tho, malware can collect info, spy on activity, eavesdrop on communications and even reroute network traffic. (Yes, that includes Macs.) It's not unusual to find Koreans scanning your ports, cookies from countless unwanted sources, or servers horning in on web locations; these are easily stopped in their tracks. It's another matter to find something operating in a System's background secretly collecting and sending data while consuming upload bandwidth. It's something to watch for by checking network activity (Applications > Utilities > Activity Monitor).
We recently removed no less than five different variants of a malware app designed to hijack network comms on a single machine; one of those apps dated back five years. But, credit where credit is due: That particular machine had been used to explore, shall we say, "seedy" segments of cyberspace and malware was voluntarily downloaded by its owner.
Turn on your OSX firewall
(System Prefs > Security pane > Firewall tab - should be on by default), and do not allow file sharing of any kind over the internet. Sharing thru your own local area network (LAN) is fine; office networks are usually managed by in-house IT staff. Torrent, movie and music sharing sites are well-known for passing malware, so if you want some app or music - hey - buy it! No sympathy here for those who install BitTorrent, uTorrent, Limewire, Vuze and other such software. Legitimate sources consider it theft to use such things, and so do we.
If you need a 'viewer' or update, go to the source and get it
Adobe.com's Flash Player (deprecated with HTML-5) should be uninstalled.
VideoLAN has VLC for translating WMV and MS file types, and QuickTime will open most A/V files. Odds are you already have software that will do whatever you need. Avoid anything that shows up uninvited while surfing the web, including video players, warnings, "updates," or apps that claim to speed-up, clean or fix your Mac. Some of the latter are malicious.
There's only one way to absolutely guarantee total network security on any computer, and that's by disconnecting from the internet altogether (airgap). Short of literally pulling the plug on communications, remain vigilant to intercept and identify potential leaks, control access, use passwords and pay attention. Again, the #1 (and arguably only) security tool most Mac users really need is common sense.
|




 Since putting the OS into a locked partition (starting with OS 10.15 Catalina), Apple has added security features that can prevent access to your Mac. All users running OS versions after OSX should be aware of these new security features - which are active by default. Startup Security
To check Startup Security settings, startup your Mac in Recovery Mode:
Intel Macs: From OFF, press and hold Command+R during startup
Apple M1 and later CPUs: From OFF, press and hold power button for 10 seconds, then choose Options to startup in Recovery.
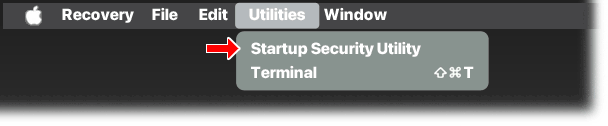 Utilities menu in Recovery Mode showing Startup Security
NOTE: Older OSX Systems may not have Startup Security; instead, there will be an option for setting a Firmware Lock (password), which is best avoided.
Once in Recovery Mode, open Utilities menu and select Startup Security Utility, then click Security Policy button to see this dialog box:
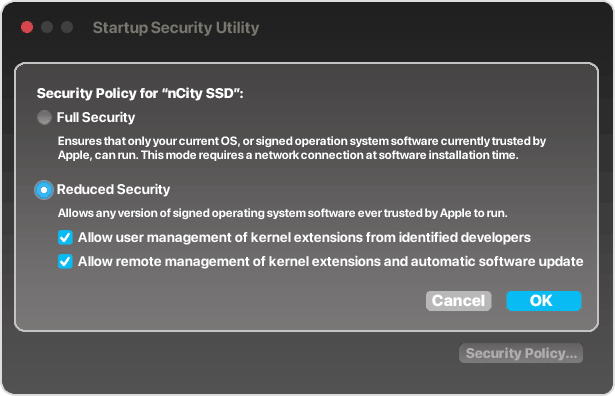 Startup Security window from OS 13 Ventura and later
Full Security setting (on by default) guarantees that no one will be able to access data on drive without assigned password. Of course, this assumes machine is fully functional; if the Mac is not fully functional, this setting locks out troubleshooting and data recovery, with or without password. Having seen many machines with broken displays, spills, and other damage, being locked out adds data loss to whatever other damage machine has suffered.
Reduced Security settings (as shown) is recommended to allow networking with another Mac or drive, step one in data recovery process and troubleshooting a damaged machine. Restart to exit Recovery Mode.
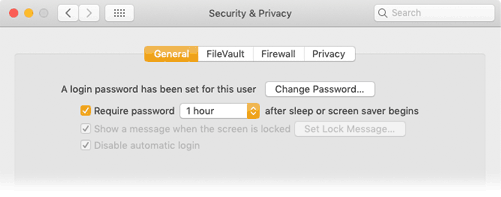
FileVault
File Vault data encryption, also on by default, is a much older security feature that's been around since about 2003 and Mac OS Panther. Is it necessary? No. FileVault is in System Preferences in older machines, System Settings on newer OS versions under Privacy &Security as shown below.
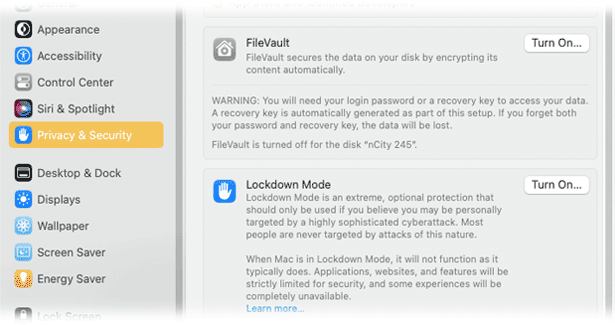
FileVault and Lockdown Mode from System Settings in OS 13 Ventura and later
FileVault is fairly stable, transparent and harmless - unless you lose or forget the Master Password. We've had clients who set a password and promptly forgot what it was. Result = SOL. Like most real security features, there is no workaround. If it's on, the "Turn On..." button illustrated here shows as "Turn Off." Turning off FileVault can take a long time, and requires the password used to turn it on.
Lockdown Mode is yet another new security feature, and this one is so extreme it is OFF by default. Apple recommends this setting for those who may be under active attack in certain circumstances. More info from Apple here and here, but for the vast majority of us, this feature should be left off and ignored.
NOTE: Upgrading to Sequoia may "lock" your Time Machine backup drive if it is a rotational drive from prior OS versions (this issue is developing). Suggest a new SSD backup drive for OS Sequoia and later. Some report backup drive is still available when connected to an older OS, and data should be intact.
|